The oil and gas industry faces technical challenges unique to its business, with hundreds of thousands of onshore and offshore wells distributed over wide geographic areas and thousands of miles of pipelines requiring continuous monitoring, periodic maintenance, and constant connectivity to ensure safety and optimized performance. As new, Internet-enabled technologies emerge to help address the operating challenges in these environments, companies must consider carefully the emerging risk of significant cybersecurity breaches in order to avoid or minimize the monetary, reputational, and operational damage from such intrusions. While additional computational and networking capabilities will drastically change how businesses operate in the future, the tradeoffs inherent in deploying such technology must also be kept in mind.
The connectivity of all of our myriad devices, known as the IoT, has advanced dramatically for corporations and households alike. Micro-sized devices, heavily equipped with electronic and networking components, are increasingly becoming embedded into our working and personal lives. While the consumer implications are broad and increasingly visible, businesses are also improving their processes with increased automation and advanced analytics that take advantage of concepts such as predictive maintenance or near-real time monitoring of infrastructure.
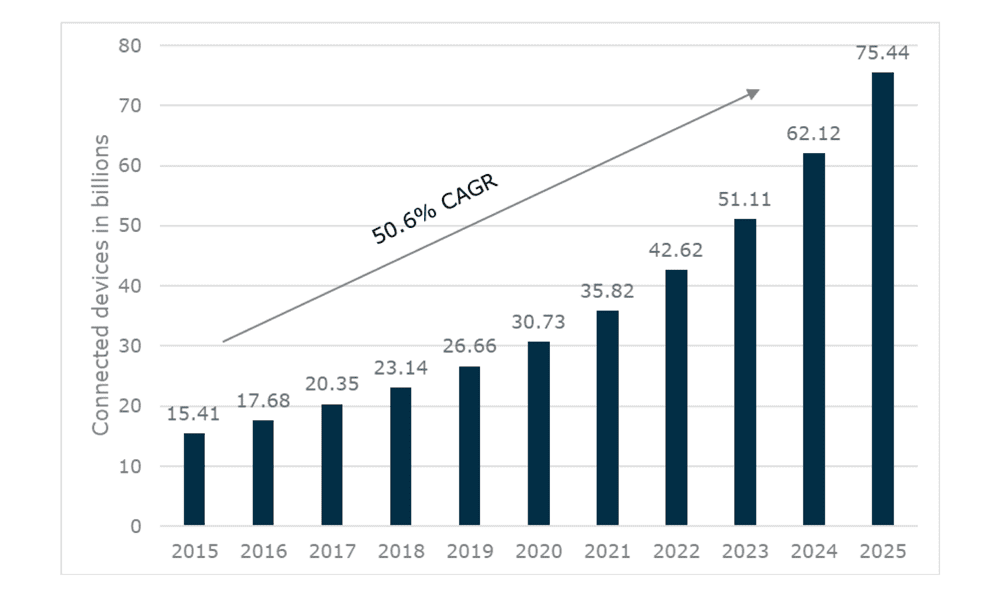
As we move from early adoption into general acceptance, the number of IoT devices continues to grow at an exponential rate. Only three years ago, there were 15.41 billion IoT devices connected worldwide; now however, according to Statista, the 23.14 billion devices installed in 2018 will grow to more than 75 billion by 2025. There is little debate over the benefits that can be realized by using these devices. However, corporations often overlook critical security considerations when deploying new, cutting-edge technologies, and IoT devices are no exception. The importance of considering security implications may not always be clear in the initial deployment of such technologies, particularly when executives are focused on the opportunity to reduce costs and increase their bottom line.
Growth in IoT Devices
Lacking security-related analysis, a breach on a connected device could allow hackers to steal data, disrupt operations, and impact production. Seasoned adversaries will often seek entry on an unsecured connected device in order to expand their access to sensitive databases and file structures in other locations. Popular IoT device developers claim that the security protocols that their hardware utilizes are fully secure and, in some instances, “future proof.” In reality, without adequate security practices in place to support their use, these devices may actually be easy to compromise, as demonstrated by the SANS Institute1. As a result, it is likely that many organizations have not adequately quantified the risk resulting from their growing reliance on IoT devices. Data breaches are in the news far too often, and companies are suffering major impacts to their stock value, reputation, or operating earnings as a result. These impacts are particularly acute in industries that require an always-on, always-functioning infrastructure, where any disruption can cost hundreds of thousands, if not millions, of dollars per incident.
In the news, we have seen examples of attacks focused on shutting down connected devices. TSMC (Taiwan Semiconductor Manufacturing Company), the world’s largest manufacturer of semiconductors, was forced to take multiple plants offline in order to recover from an attack.2 Saudi Aramco, one of the world’s largest oil companies, suffered one of the largest hacks in history in 2012. The hack originated on a single computer that was connected to their larger IT infrastructure, wreaking havoc throughout the network. As a result of the breach, Saudi Aramco was forced to take a number of their operations offline and had to resort to the manual handling of supplies, shipping and contracts with governments and business partners. Approximately 35,000 computers were affected, forcing the company to give oil away for free, in some cases, to avoid disruption in distribution.3
This leads to an interesting challenge in the oil and gas industry, where companies will be keen to harness the significant benefits that IoT devices bring but must simultaneously work to protect their infrastructure from the expanded attack surface presented by the same devices.
For example, within the past few years, upstream and downstream oil and gas companies have seen an evolution in the technology available to monitor and automate operations. Companies are implementing this new technology to reduce NPT (non-productive time) by integrating information and operational technology to speed up processing time, to enable predictive maintenance, and to reduce frequency of disruptive incidents. Additionally, to prevent/minimize disruption, companies typically supplement manual inspections with PLCs (programmable logic controllers) to control valves and satellite connections to remotely monitor equipment – greatly improving overall operating efficiency. While the operational benefits from such initiatives are easy to measure and report, the risks of inadequately protecting this expanded attack surface are not often considered fully – raising the specter of operational disruption and loss of key assets.
Operational disruption is not the only risk posed by insecure devices. As the energy industry is already heavily regulated, additional fines and repercussions are likely to be explored by regulators concerned about the systemic risk of a vulnerable infrastructure. The NERC CIP (North American Electric Reliability Corporation Critical Infrastructure Protection) protocol provides a set of requirements designed to better secure the assets that operate North America’s bulk electric system. The protocol also stipulates the need for robust cyber capabilities to protect, detect, and recover all critical systems. Similarly, purchasing cyber insurance, while somewhat beneficial, is not a one-stop shop for mitigating fines and profit loss resulting from a cyber breach because residual mitigation and recovery efforts can continue to incur costs. And how do you quantify the potential, ongoing reputational and brand impact of such an incident?
Now the question becomes, what can organizations do to mitigate the risk stemming from this growing reliance on IoT devices? As technological capabilities evolve to more fully automated monitoring of operating conditions and to more advanced analytics and machine learning capabilities, security programs must also mature and enforce the concept of “security by design.” That is, IoT devices supporting communication and storage should have appropriate security layers in place. Sensitive data must be segmented from less secure networks, and any transmission of data over any network should be end-to-end encrypted. Security can’t be locked into the firmware, future-proofing requires upgradeable measures to address currently inconceivable new threats. Additionally, ongoing, real-time monitoring and automated incident alerting on IoT devices can enable timely response to any suspected compromise. Proper security testing, mimicking real-world scenarios, must include assurances that IoT devices and their supporting infrastructure are regularly scanned for vulnerabilities and upgraded when necessary. All these defensive measures need to be defined and documented, while driven by a security policy that aligns to both business and security objectives of the organization.
What You Need to Know
- While the use of IoT devices within industry are growing exponentially, for all the cost cutting and strategic benefits they provide, these devices, and their connections to the internet, are not inherently secure.
- A breach of a connected device has the potential for exponential damage as the impact traverses industrial and IT systems to which it connects.
- The solution is to plan ahead, to consider security throughout the design, and to monitor in real time (security-by-design and defense-in-depth).
- New cyber laws and regulations are being implemented on a continual basis.
1 – In order to demonstrate the importance of proper security testing and design, SANS developed a series of straightforward exercises to demonstrate the relative ease of compromising a device leveraging the Thread protocol, a common IoT medium. SANS [https://www.sans.org/reading-room/whitepapers/internet/gorilla-deliver-assessing-security-googles-thread-internet-things-iot-protocol-38070]
2 – ZDNet [https://www.zdnet.com/article/tsmc-says-variant-of-wannacry-virus-brought-down-its-plants/]
3 – CNN [https://money.cnn.com/2015/08/05/technology/aramco-hack/index.html]
Bill Ebanks is a managing director in the Energy Practice atAlixPartners, the global consulting firm.
David Head is a managing director in the Digital Practice atAlixPartners, the global consulting firm.